All the big shots, I am a new person, white, seeking guidance!!!
A local police department received a complaint from a victim that he was defrauded on a virtual currency trading website, which claimed to use ‘USTD Coin’ to purchase the so-called ‘HT Coin’. After the victim topped up, not only could the ‘HT Coin’ not be withdrawn or traded, but his mobile phone was also locked and ransomware was maliciously installed. The police investigated the case based on the virtual currency trading website provided by the victim and conducted an investigation into the case.
According to the website domain name and IP provided by the complainant, the police retrieved the corresponding server image ‘Material 1’ and analyzed the materials in hand to answer the following questions
Use FireEye directly to get it
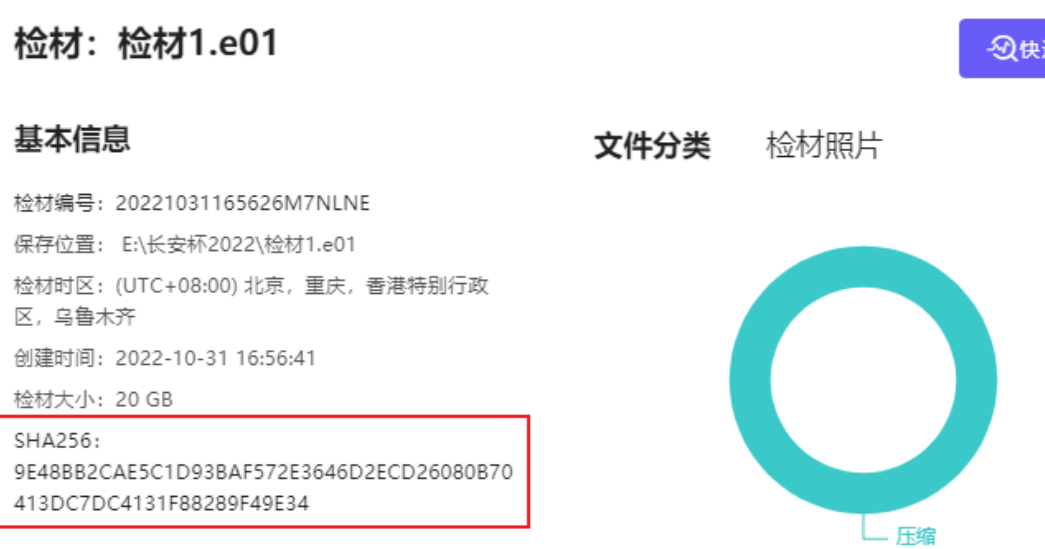
You can check the IP in the login log to see that they are all the same, so it is determined that the IP address of the technical personnel is: 172.16.80.100
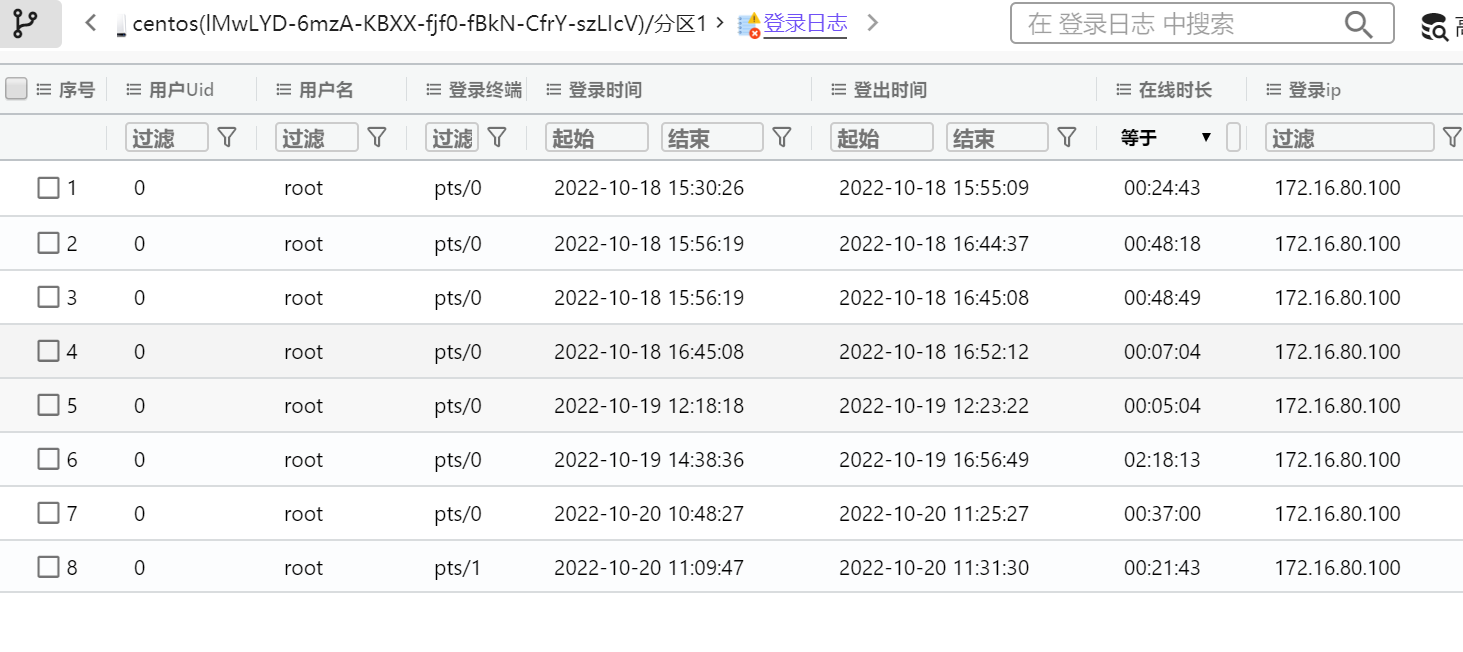
Or simulate the last command to get 172.16.80.100
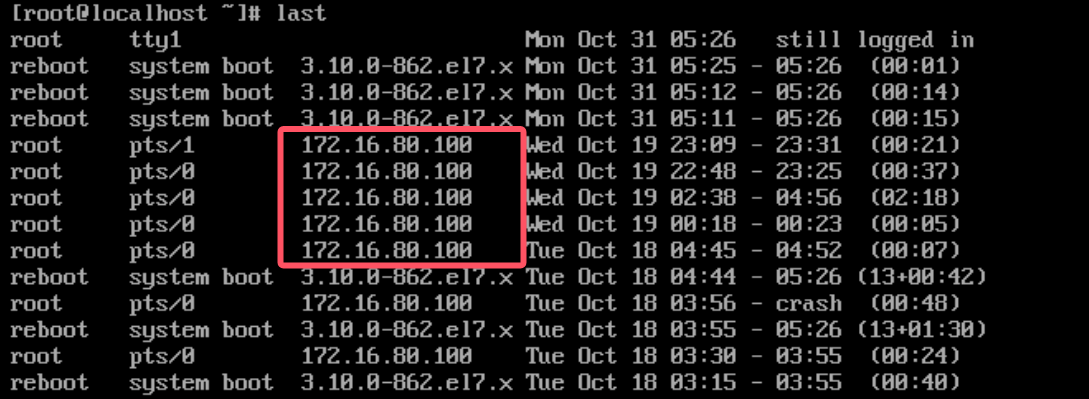
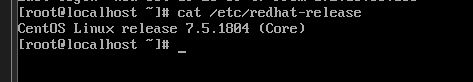
7.5.1804
Or simulate input commands
cat /etc/redhat-release
Simulate ifconfig

Or view the analysis software
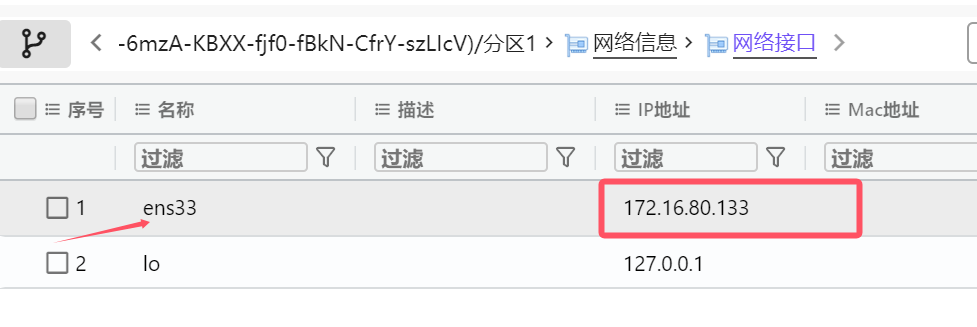
The result is 172.16.80.133
online casino platform and Where is it
By viewing the history commands and filtering the keyword jar, it is found that the directory /web/app/ is frequently accessed, command history |grep jar
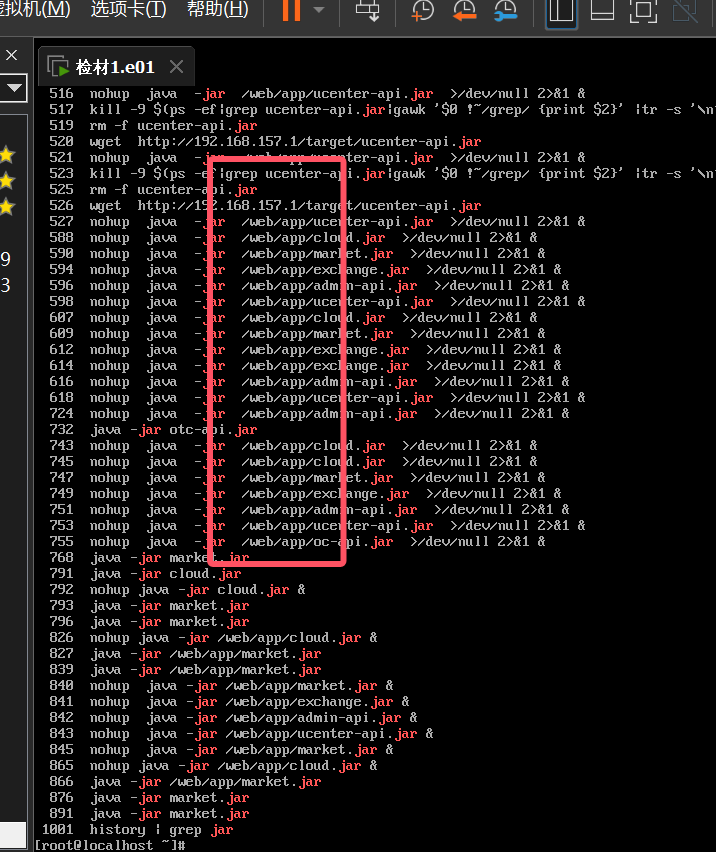
The result is /web/app/
Export all jar packages, analyze them one by one, and check which jar package uses the 7000 port

After exporting, check that 7000 port is used in cloud.jar
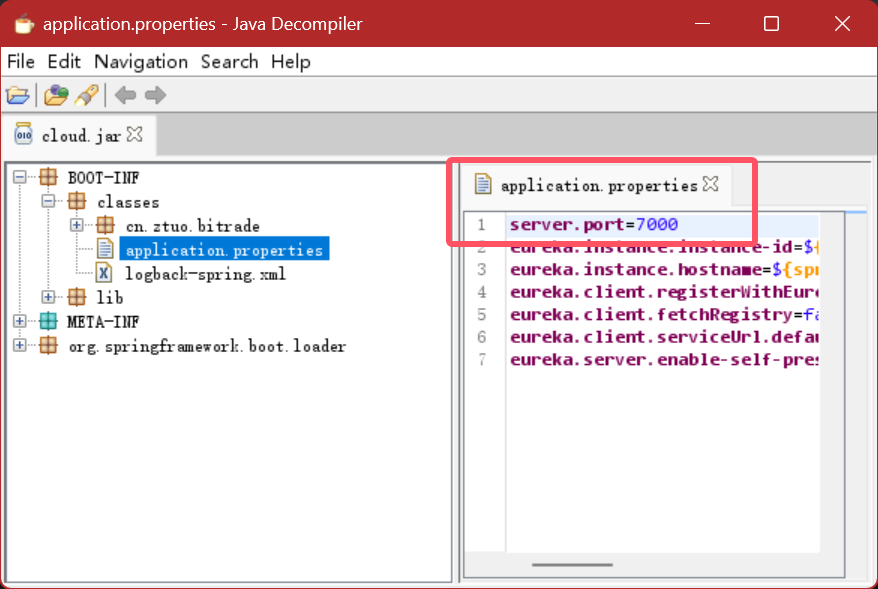
cloud.jar
For this question, first go to Material two, in the Google Chrome history of Material two, you can see that the background management corresponds to port 9090, and the access address corresponds to the static IP of Material one
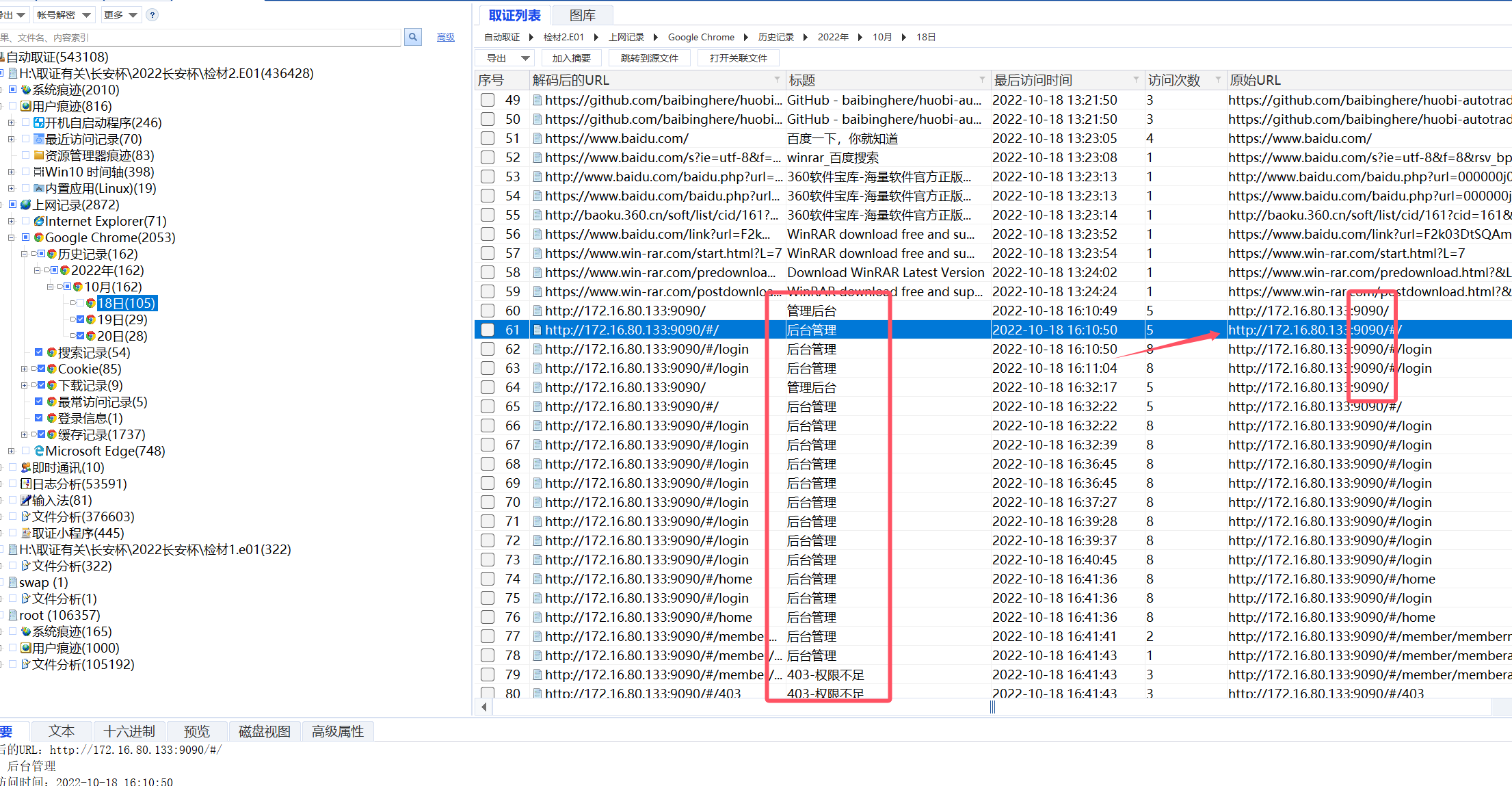
9090
After reconstructing the website, you can open the front-end page
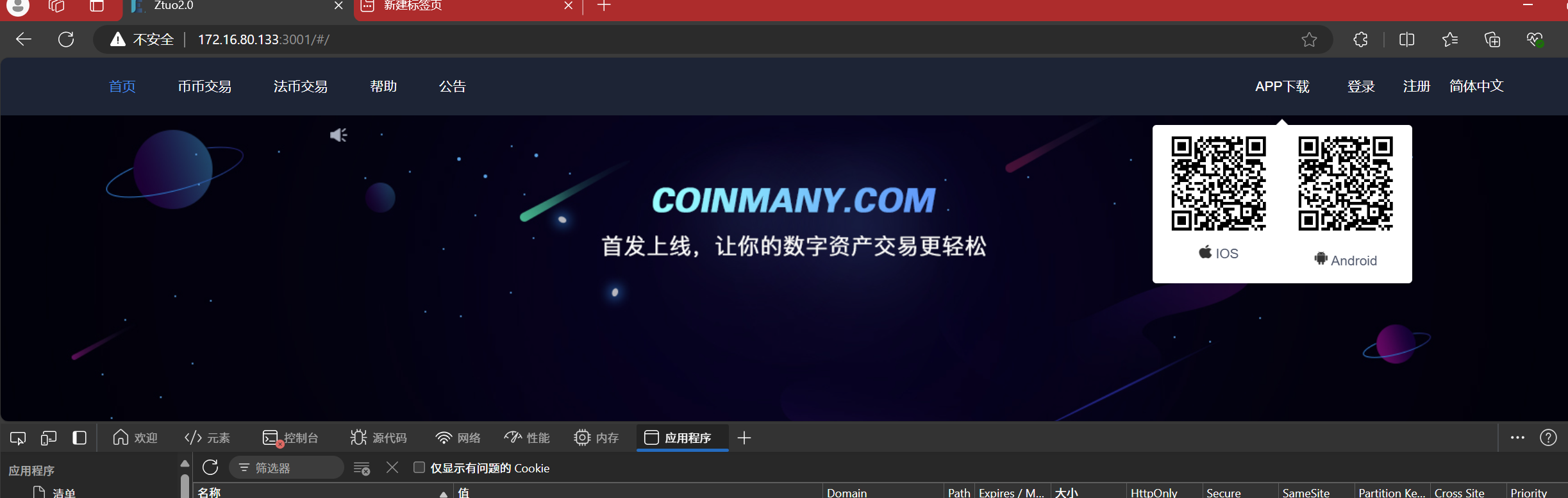
Take a screenshot of the QR code and decode it using an online website
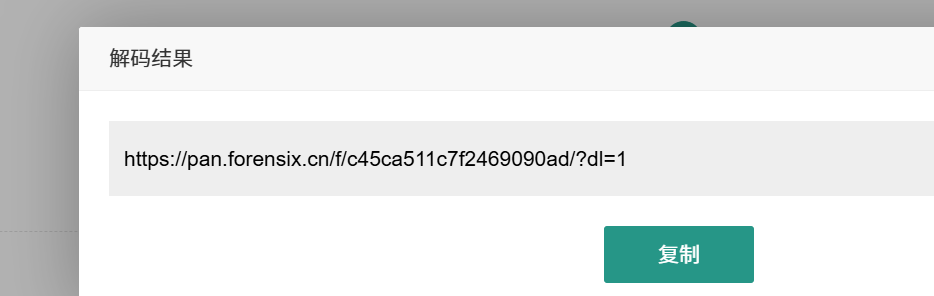
https://pan.forensix.cn/f/c45ca511c7f2469090ad/?dl=1
In this case, directly decompile the admin-api.jar package, and at the end, find md5.key, which is judged as md
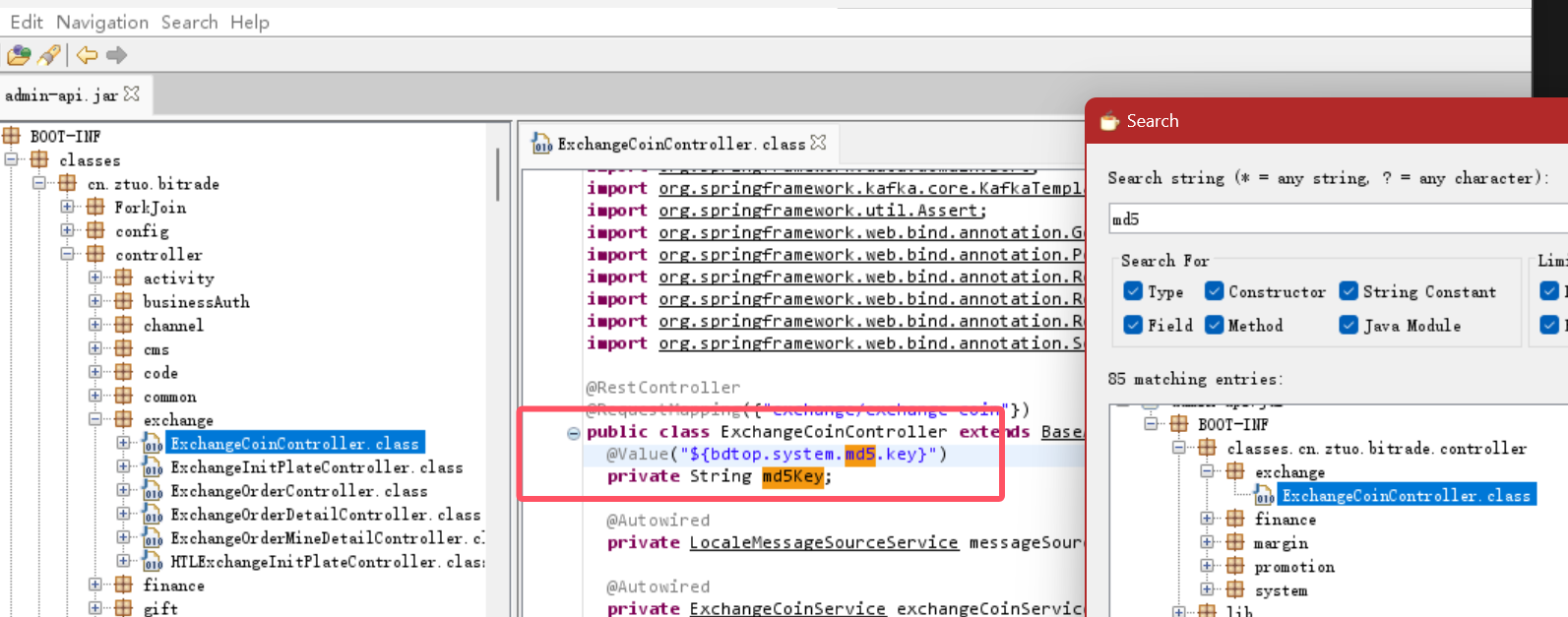
md5
Analyze the code, hahaha!!!online casino entrance,We need you

XehGyeyrVgOV4P8Uf70REVpIw3iVNwNs
Based on the IP address location and subsequent investigation, the technical personnel who set up the website were arrested, and their personal computer was seized and an image ‘Material 2’ was made. Analyze all the materials in hand and answer the following questions
Material two is obtained by decompressing the answer to the second question
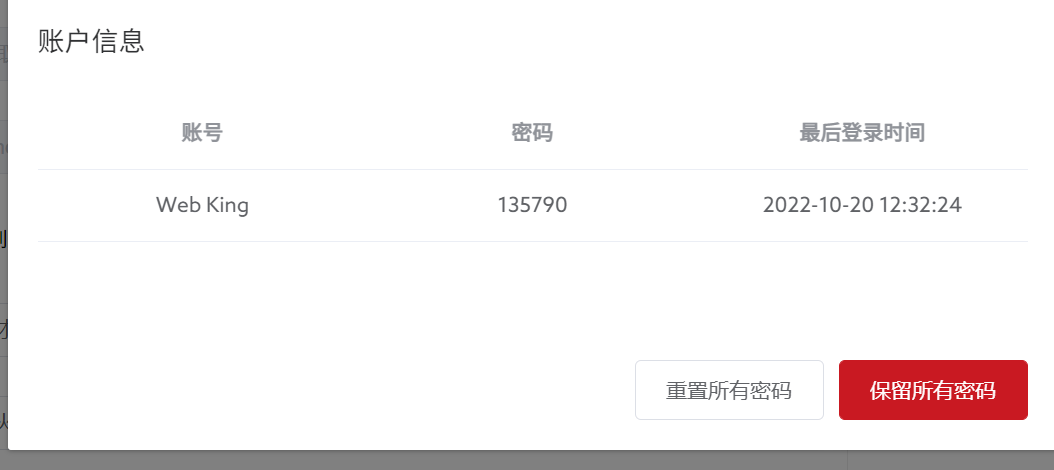
The password is 172.16.80.100
Here it can be seen directly

Or the fire eye simulation can also be seen
lottery methodThe latest plan
From question 4, we know that the IP of material 1 is: 172.16.80.133
Then exclude 172.16.80.133 from the analysis results, and the other IP is the answer
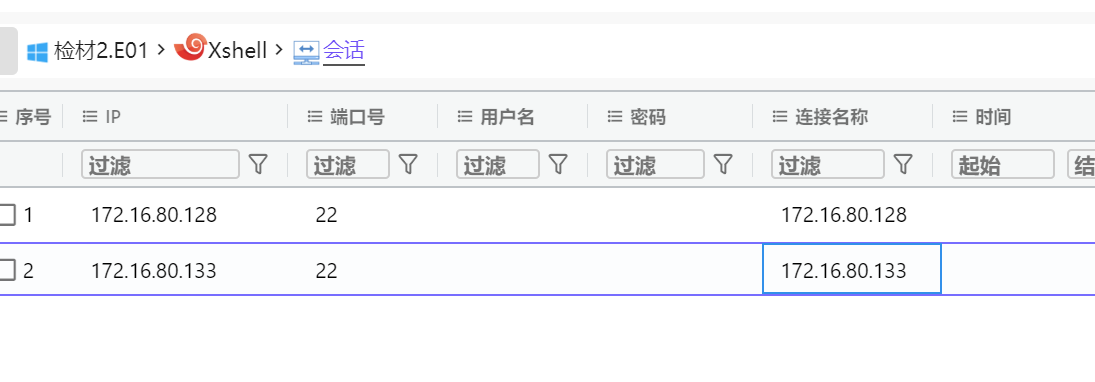
172.16.80.128
A piece of knowledge
Powershell will save the history command file under the user directory AppData\Roaming\Microsoft\Windows\PowerShell\PSReadLine, and checking the file can find the last used command

ipconfig
We can view it in the fire eye, and find the download record in the Google browser
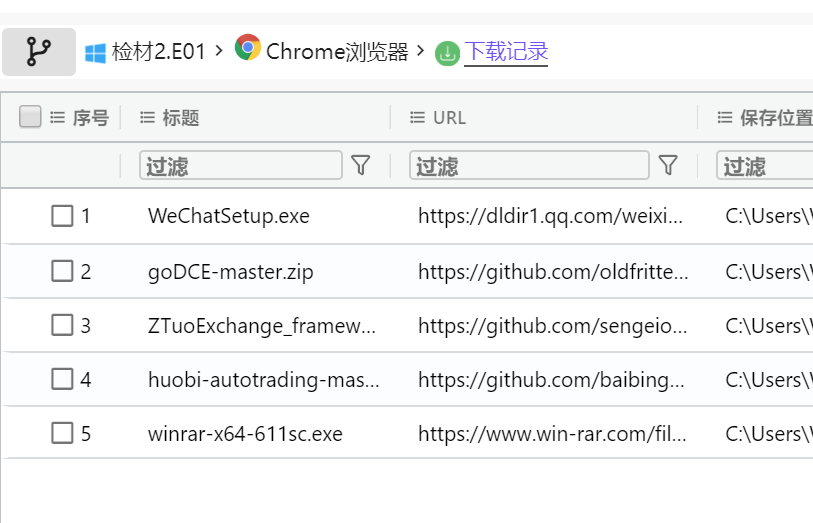
Or directly simulate and view the download
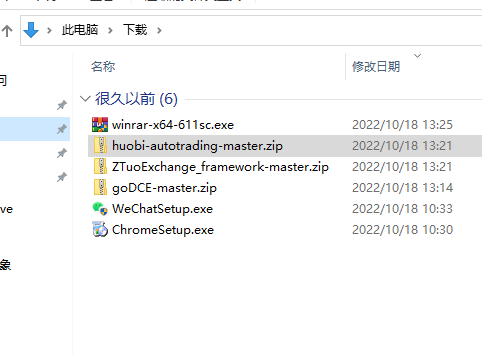
According to the question, we found that ZTuoExchange_framework-master is related to Online casino and How to find it, so it is

ZTuoExchange_framework-master.zip
This fire eye can be directly extracted

After simulation, we can get it by using the command wsl -l
Ubuntu 20.04
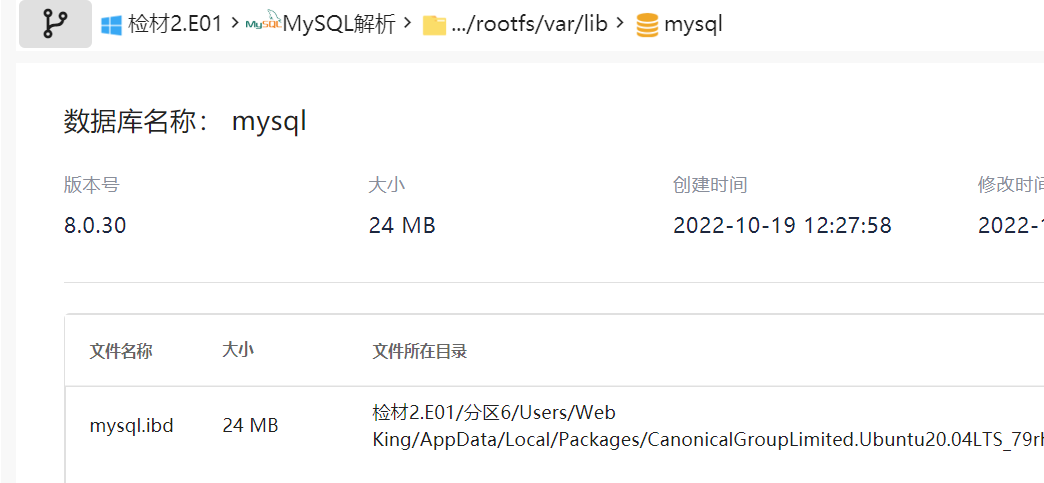
This can be directly checked with fire eye
8.0.30
The initial password of mysql’s debian-sys-maint is saved in the configuration file debian.cnf in the mysql directory
The database is running in the wsl subsystem, so we need to locate the subsystem directory
C:\Users\Web King\AppData\Local\Packages\CanonicalGroupLimited.Ubuntu20.04LTS_79rhkp1fndgsc\LocalState
ootfs
We found /etc/mysql/debian.cnf

We can find it by looking at the history of commands
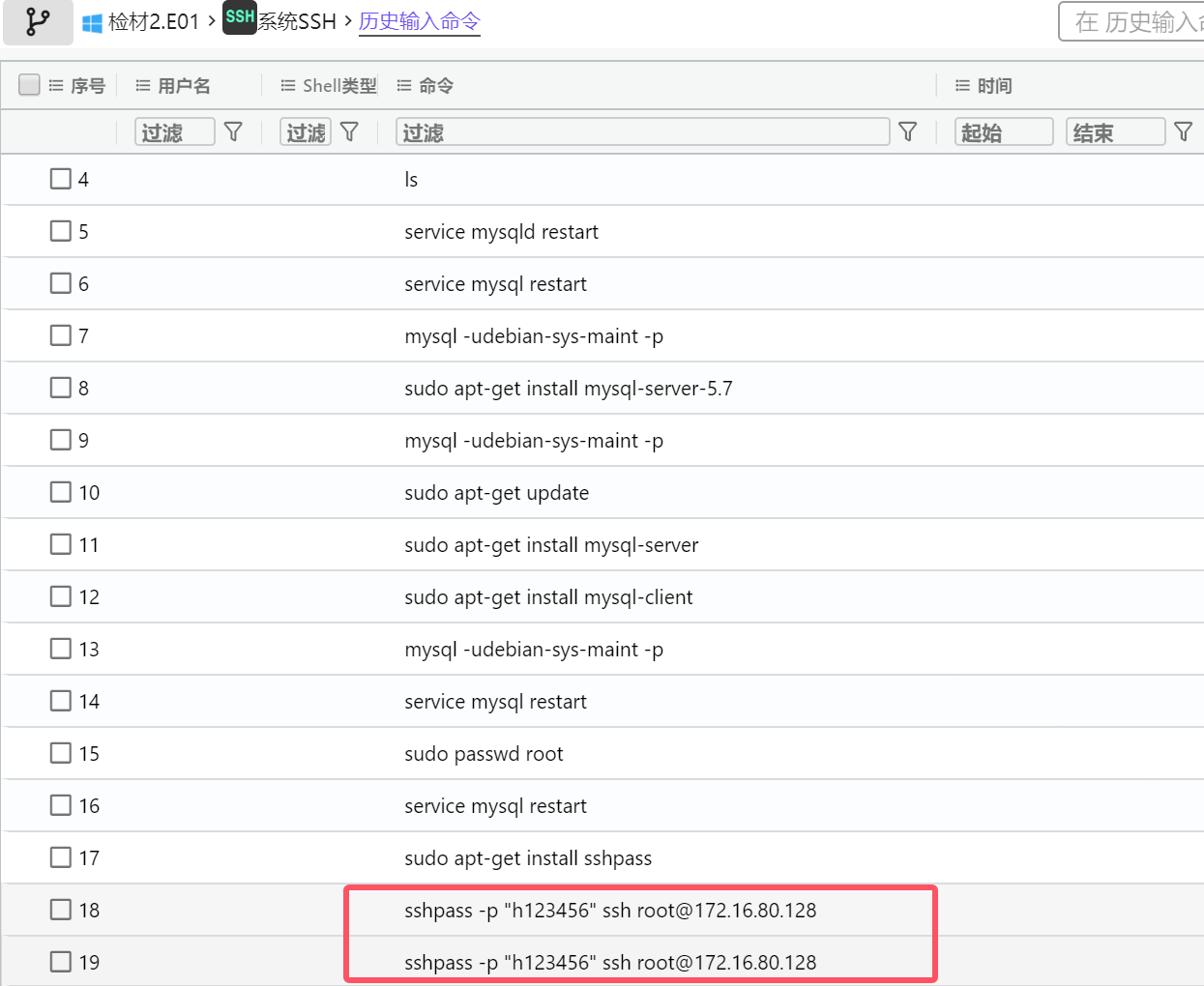
sshpass -p “h123456” ssh root@172.16.80.128
According to clues from the website frontend and the technician’s personal computer, we found the server IP of the website backend and obtained ‘material 3’ again through verification, analyzed all the materials in hand and answered the following questions
According to the answer to question 12, we decompressed material 3
The password is 172.16.80.128
First check the history of commands
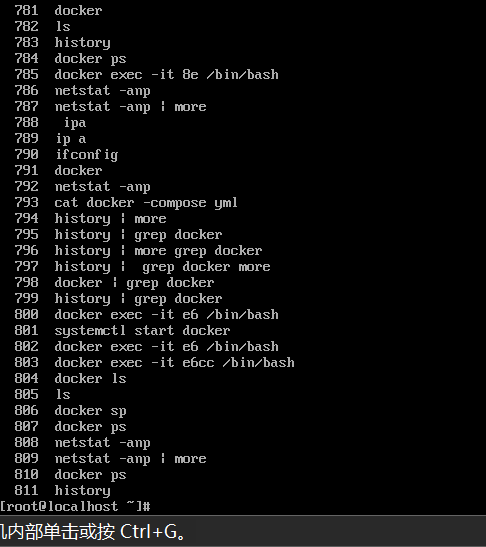
We found the docker command, started docker and checked the port
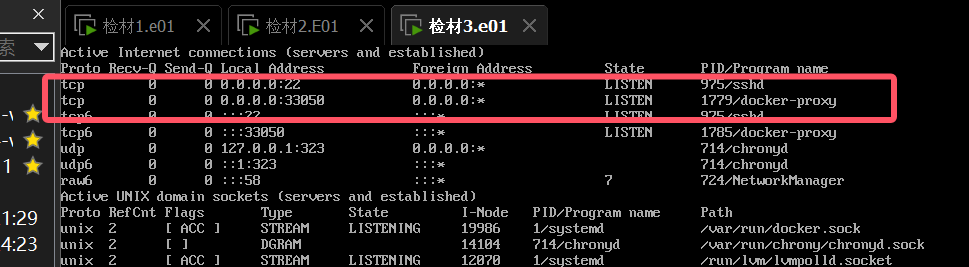
The result is docker-proxy
This is really a headache, it took a long time to figure it out, and I asked many big shots
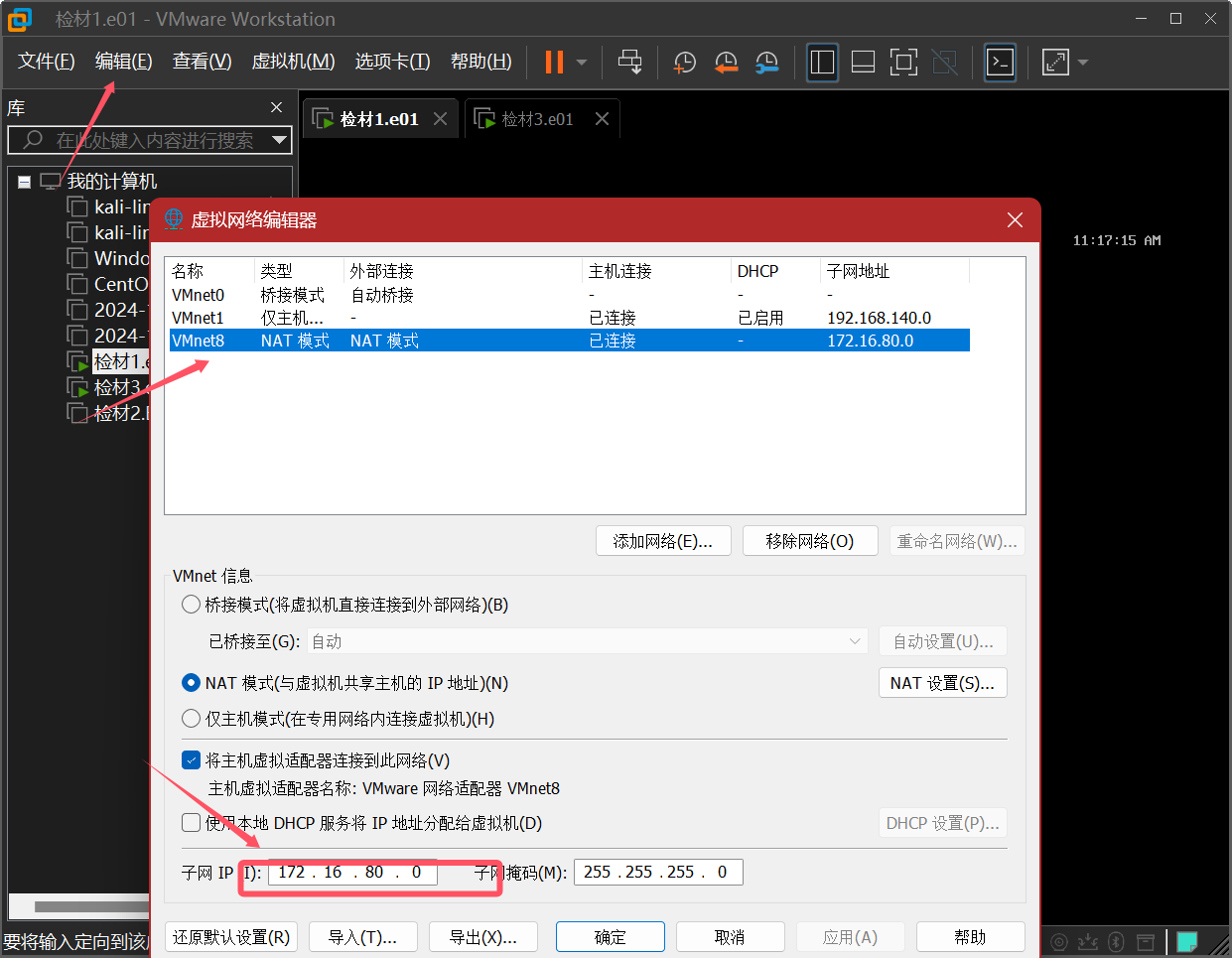
First adjust the virtual machine network, and set the virtual machine to nat so that it can be connected
We found the website construction notes, the deleted start_web.sh, and the b1 database file in the material two
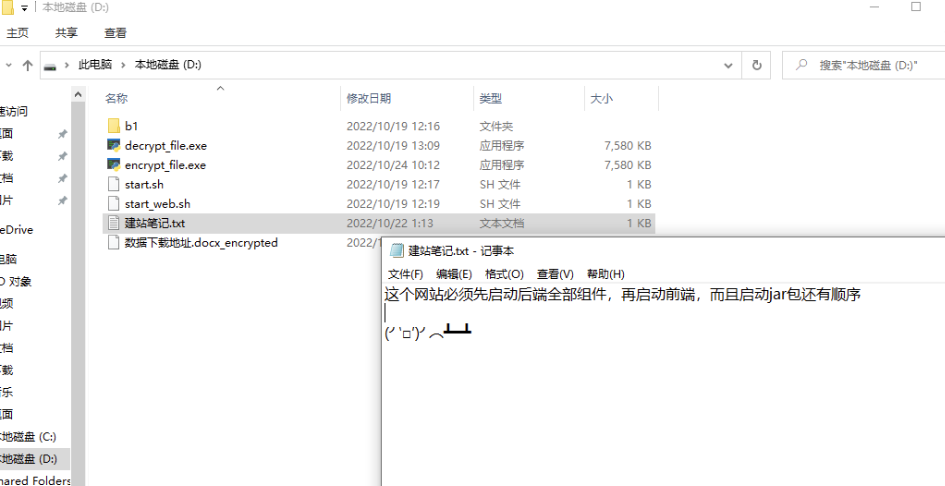
We followed the instructions in the website construction notes, first opening the backend and then the frontend, and copied start_web.sh into the /web/app directory of the material one
Then you need to give execution permission to execute
cd /web/app
chmod 777 start_web.sh
https://www.cnblogs.com/gsxmuzili/p/start_web.sh
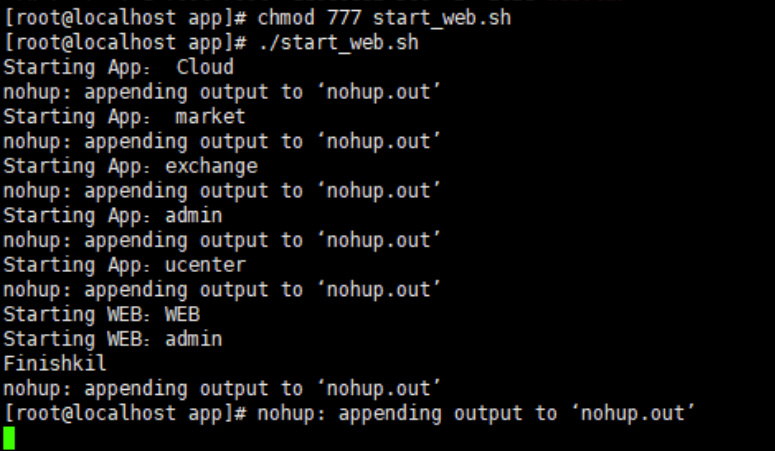
In the historical commands of material 1, npm run dev appears frequently, which is used to start a vue project. After starting, you can access the web page.
Start the front-end
cd /web/app/web
npm run dev
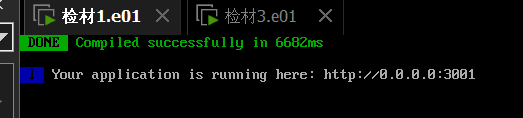
Accessing port 3001 is the front-end, and port 9090 can access the website backend management page. The username is root, and the password is root, and you can log in.

In the analysis of the first material, in the analysis of admin-api.jar, it was found that it used redis and mongo
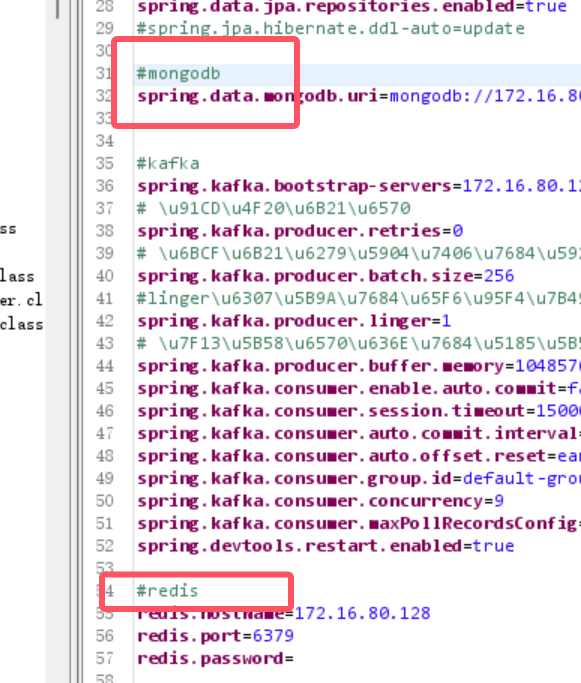
Or you can see historical command records, with mongodb and redis
Similarly, passwords can also be analyzed from admin-api.jar
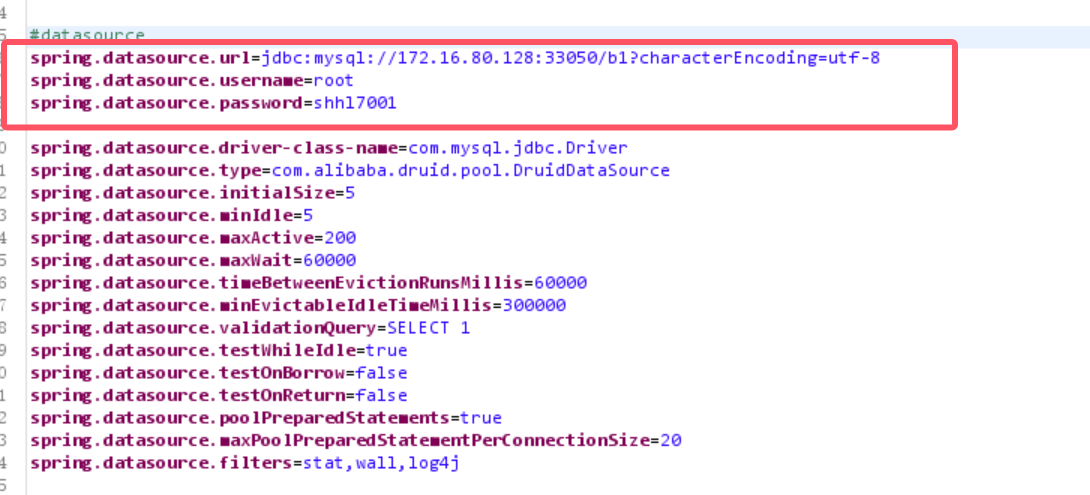
The result is shhl7001
Use the docker command to enter the container docker exec -it mysql57 bash
Then check
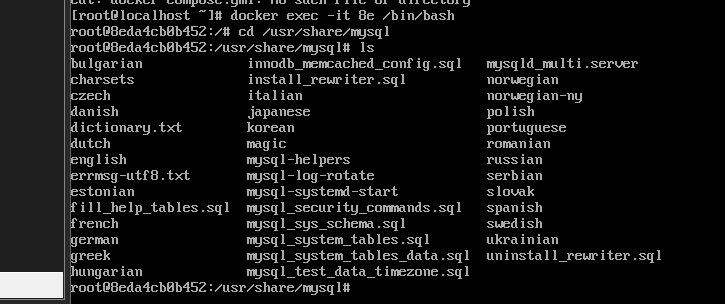
Or use the command docker inspect 8eda4cb0b452
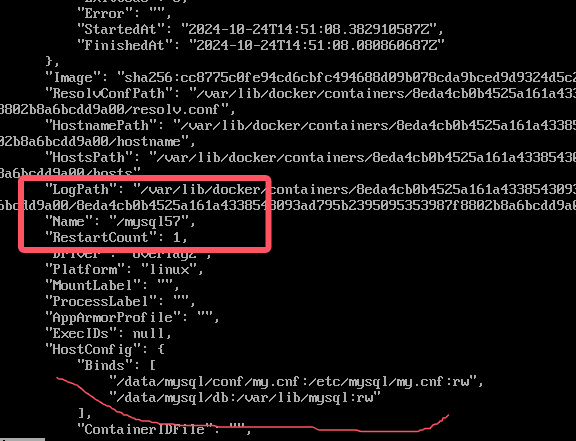
/var/lib/mysql
This question was found in a database file on the computer of the second material examined before
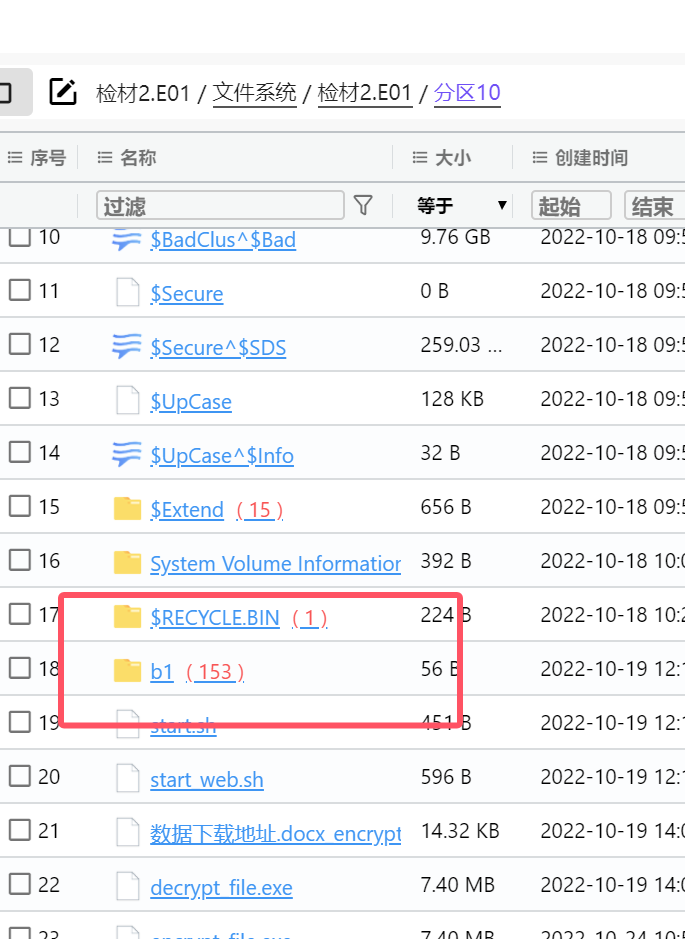
Or when analyzing admin-api.jar, you can see
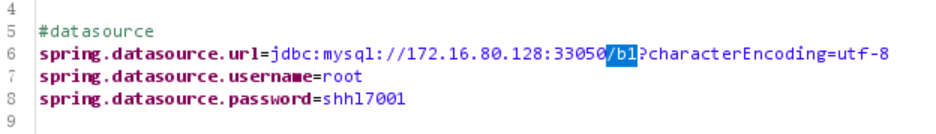
b1
First, check the database show variables like “%general%”;
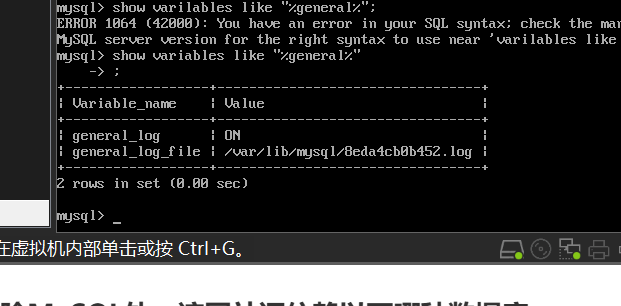
Find the log path and find the log
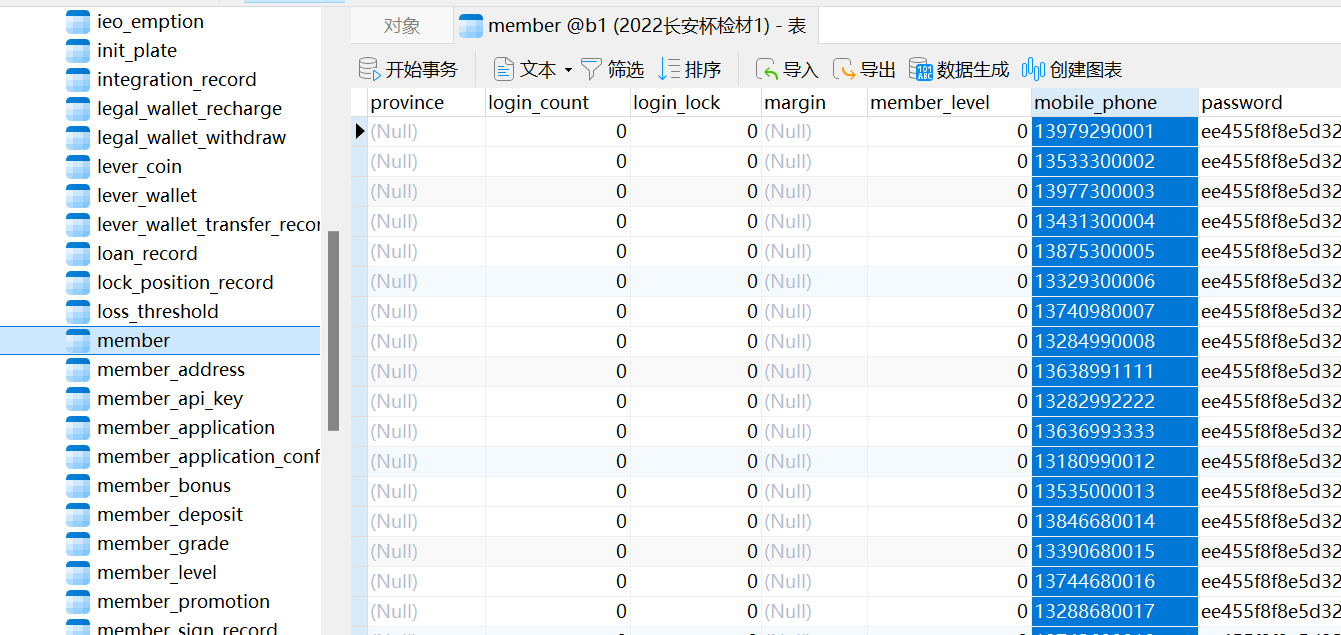
If there is a record of phone numbers in the database member, search for update in the log.
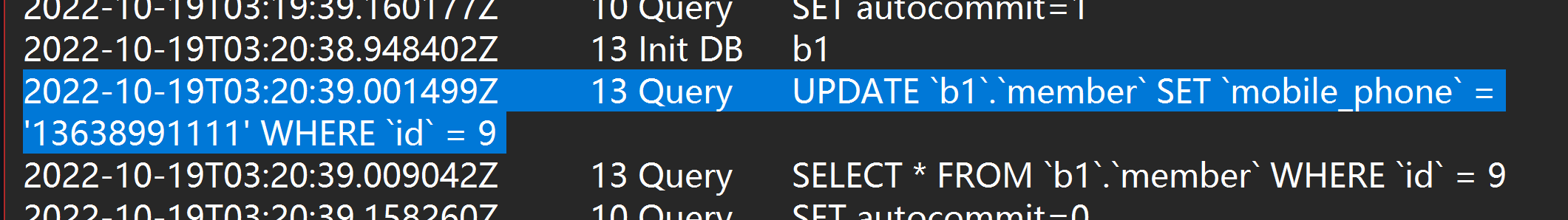
Find related data
The IDs are 9, 10, and 11.
3
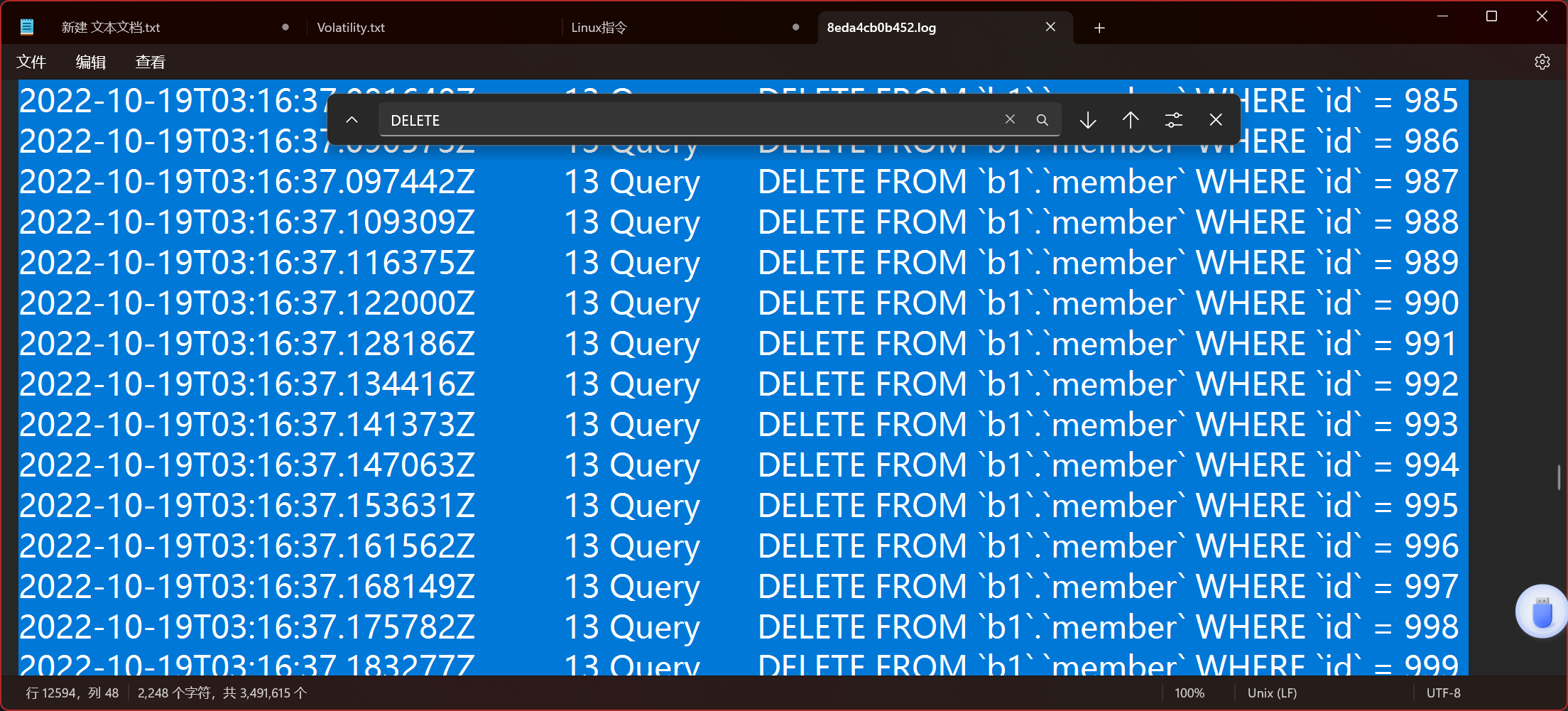
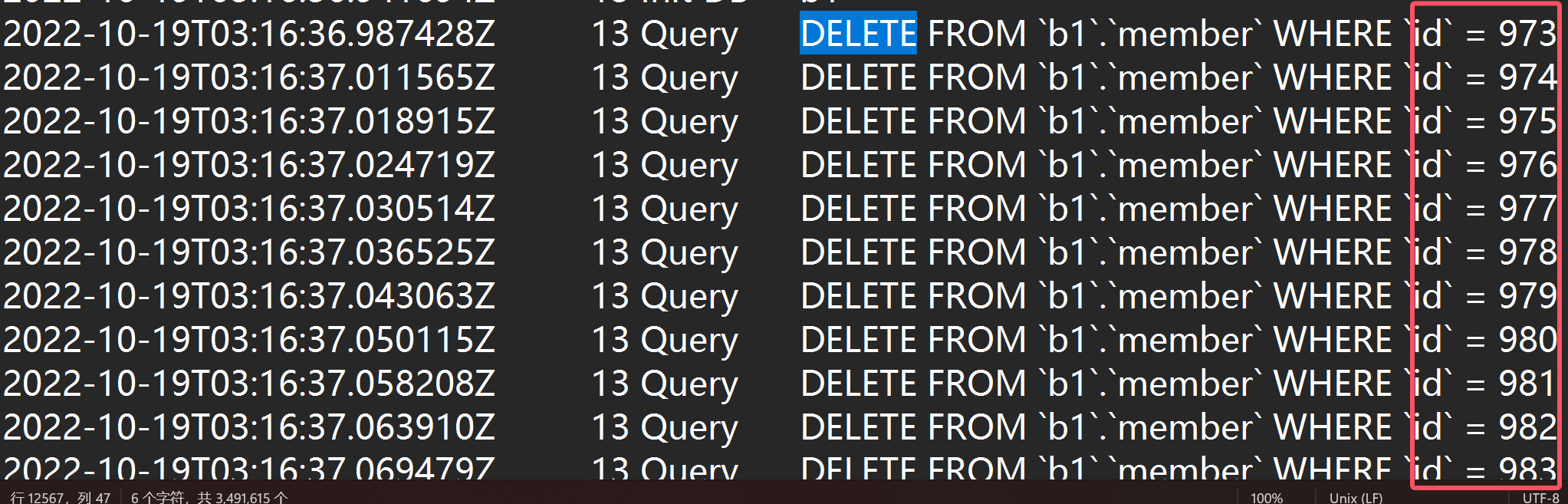
In this log, search for DELETE and you will find that he deleted the content of the member table in the b1 database, from 973 to 1000, so 28 users were deleted.
28
In the admin_access_log table of the database, 172.16.80.197
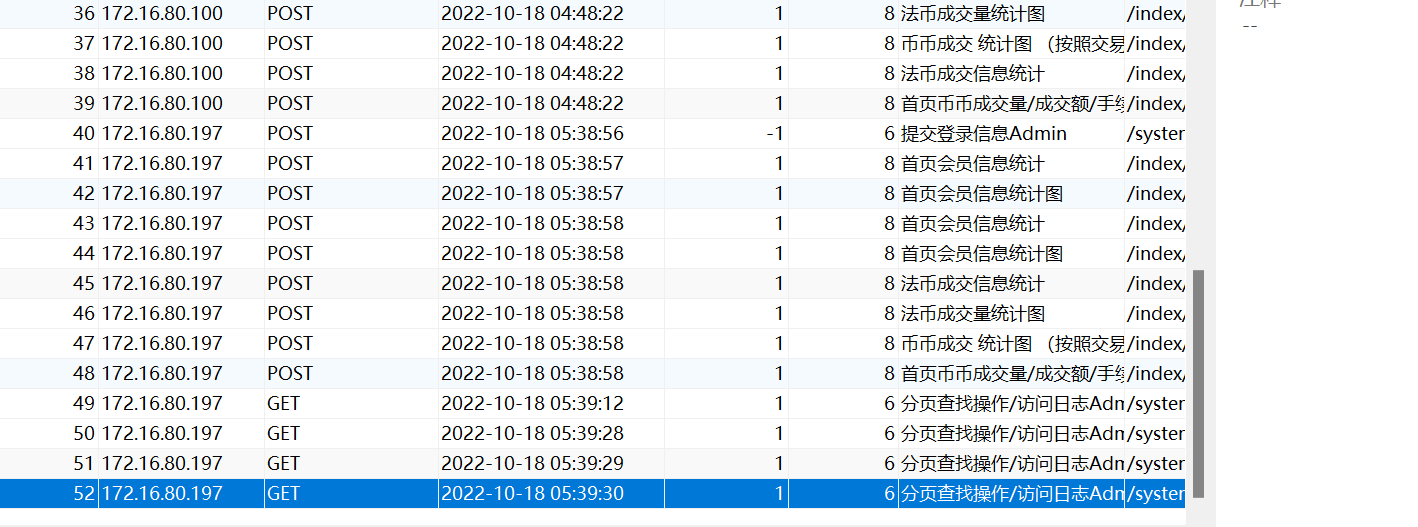
172.16.80.197
Query the member_wallet data table

cee631121c2ec9232f3a2f028ad5c89b
The answer can be found in the member table, with 158 records when member_grade_id is 3.

However, the number of users with LV=3 who were deleted was not considered. A total of 1000 records were inserted into the member table from 1 to 1000, and 28 records starting from 973 were deleted from the original table. After restoring all deleted and modified data, in question 26, we found the deleted user ID, which was a consecutive number from 973 to 1000.
It is necessary to find the original data deleted in the log, then find the number of users with member_guild_id=3, and add 158
28 deleted user records, 28 users have 6 LV3, a total of 164
Find the recharge record in membet_transaction
Then use the query statement, and find that 2 people have not recharged
The balance in member_wallet is his recharge record, find the one that is 0 for no recharge.
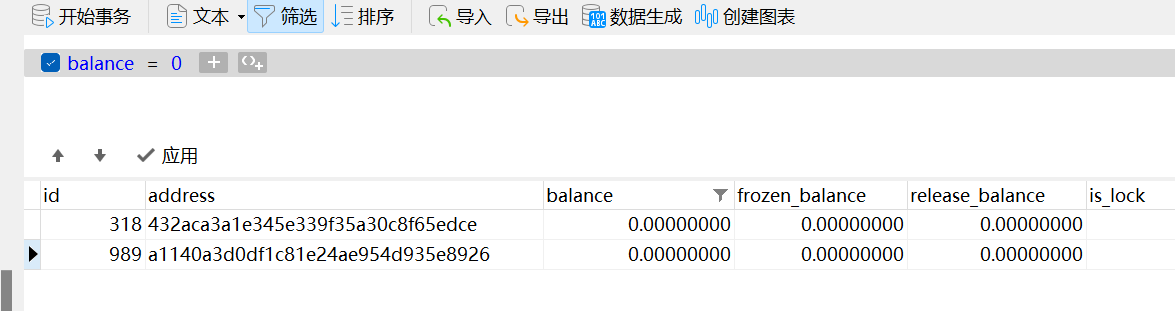
318
989
Query directly using the statement
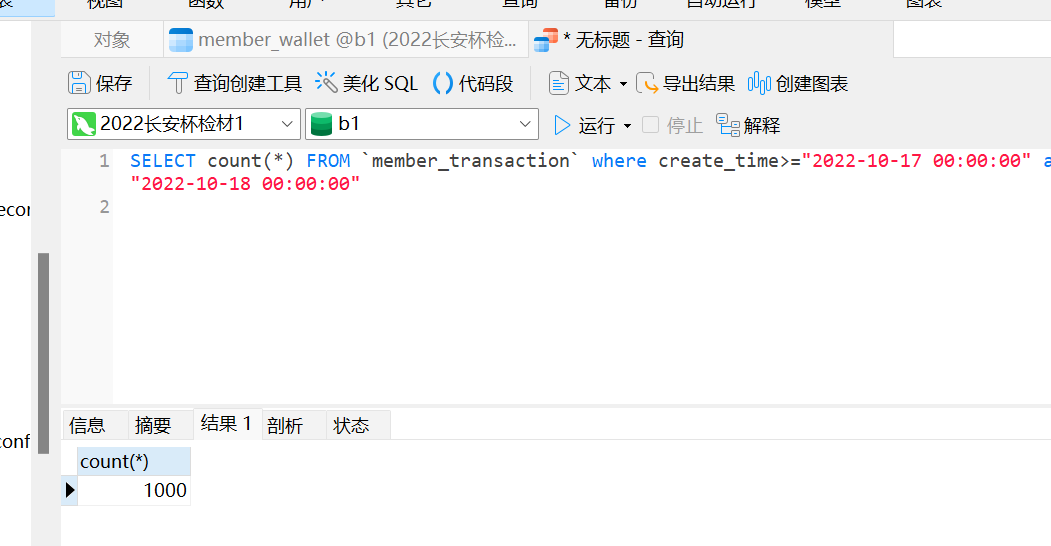
100
SELECT SUM(amount) FROM member_transaction
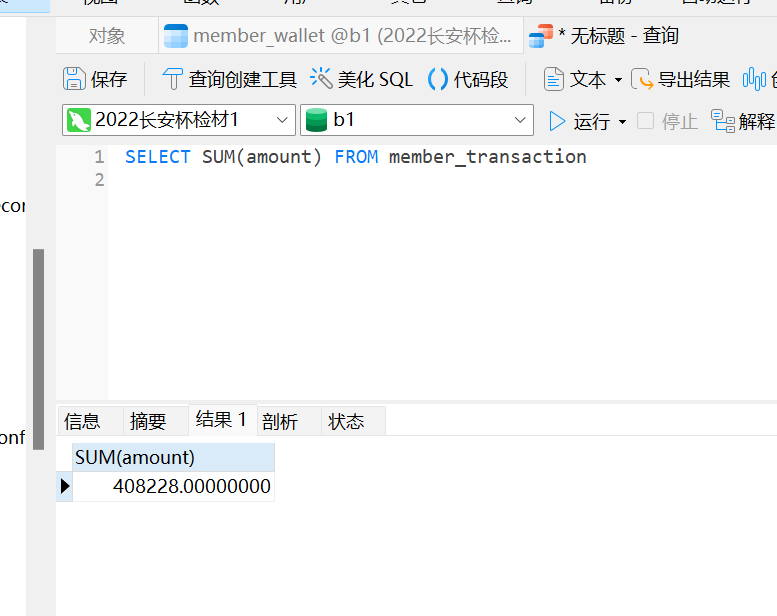
408228.00000000
According to the preliminary investigation and analysis, the boss behind the scenes was found through technical means, and the Android emulator ‘material 4’ used by him was fixed. Analyze all the materials in hand and answer the following questions
The answer to question 27 is the password for extracting material 4, 172.16.80.197
Material 4 needs to change the file extension to zip and unzip it, then put it into FireEye
Nox emulator
The npbk is the extension name of the Nox emulator backup file
Nox emulator
Through the chat records, it can be seen that
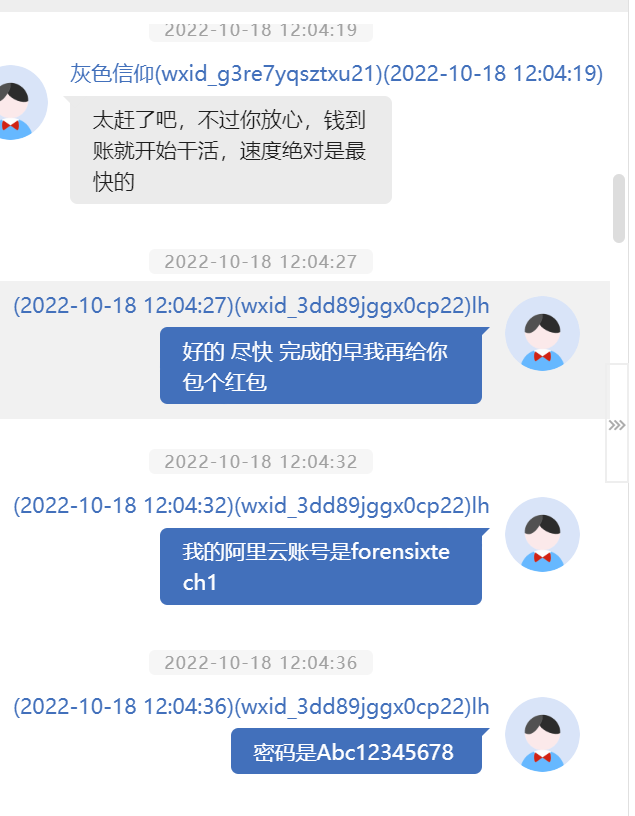
forensixtech1

v2rayNG

38.68.135.18
First use FireEye to export the apk and check the package name com.jiadi.luping

Then search in the application list

Get the installation time
2022-10-19 10:50:27
It can be found in the emulatoronline casino tutorial,We need you
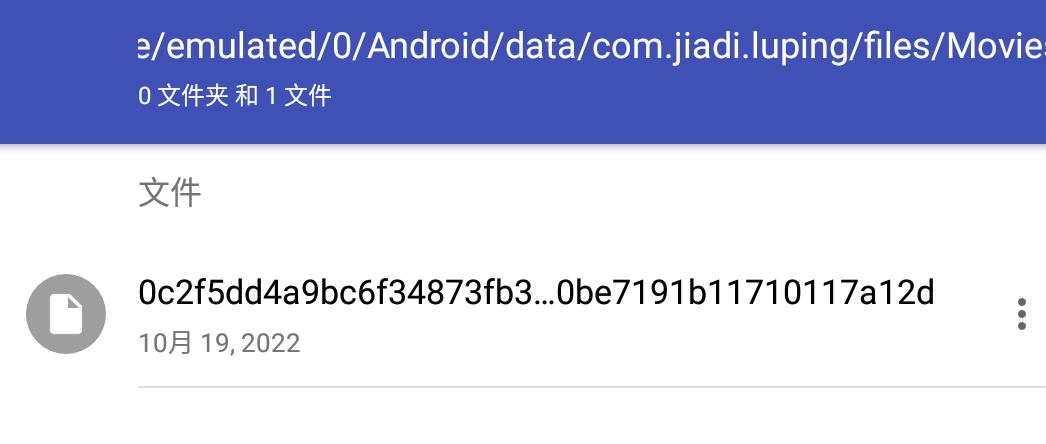
Or view it in FireEye
Analyze the database at Nox_2-disk2.vmdk/partition 4/data/com.jiadi.luping/databases/record.db, and find that it contains relevant information about the files

0c2f5dd4a9bc6f34873fb3c0ee9b762b98e8c46626410be7191b11710117a12d
View in the database
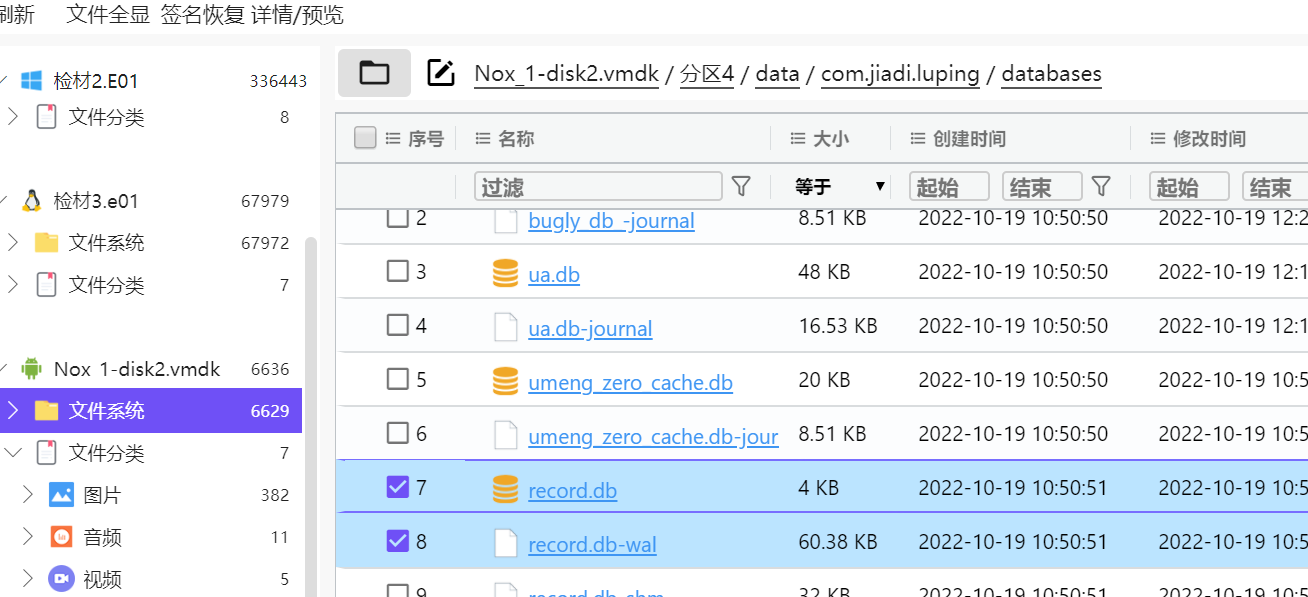
Export the record.db and record.db-wal files to the DB for viewing

18645091802
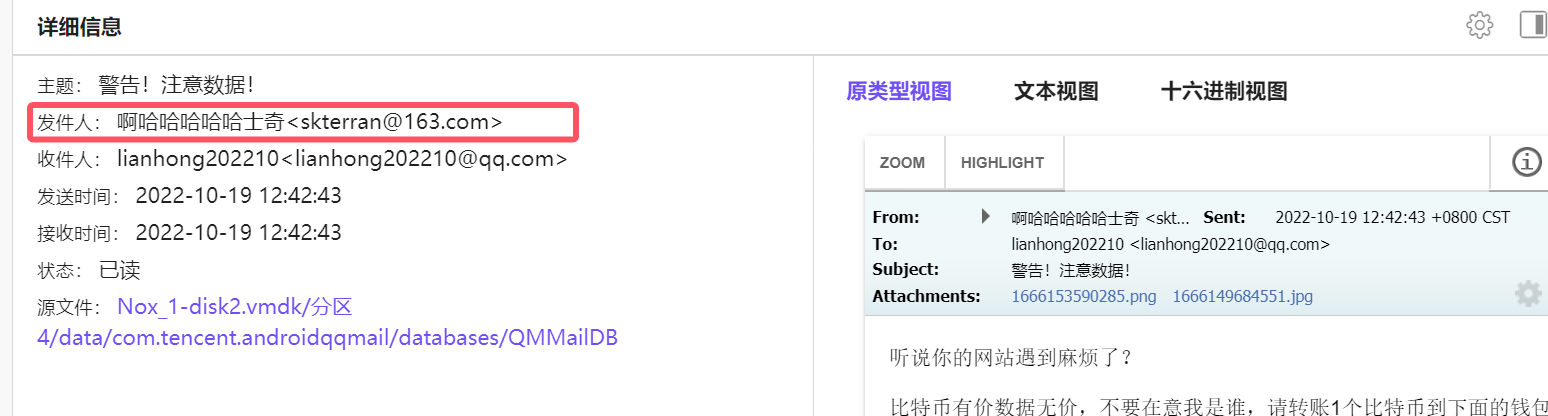
The sender of the ransomware information can be seen as skterran@163.com
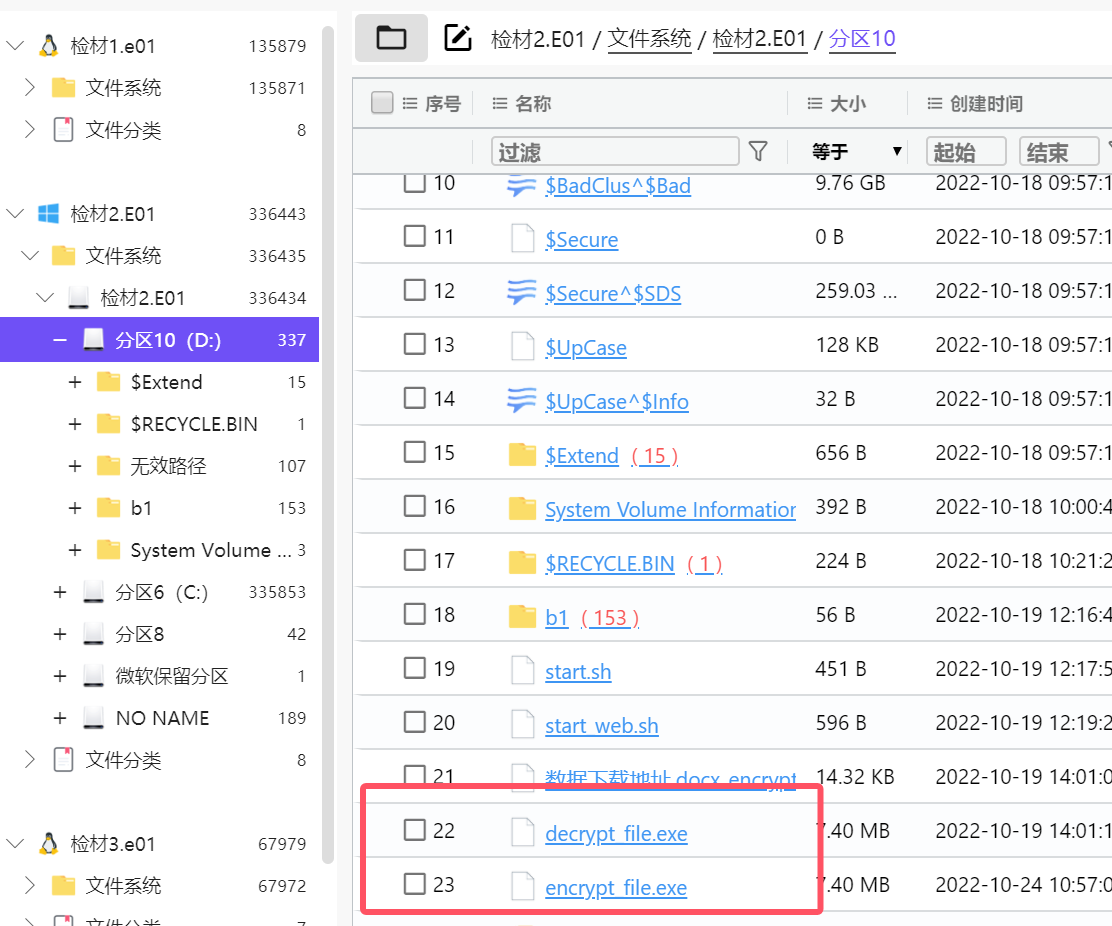
The encrypted decryption software is stored in the D disk of material 2, and there are encrypted files, export and analyze them
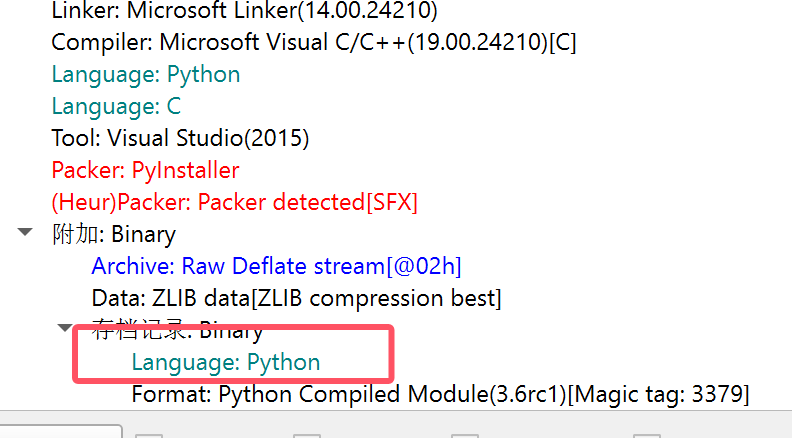
python
For the apk, there is one related to Online casino and How to find it in the material, it should be, export and take a look
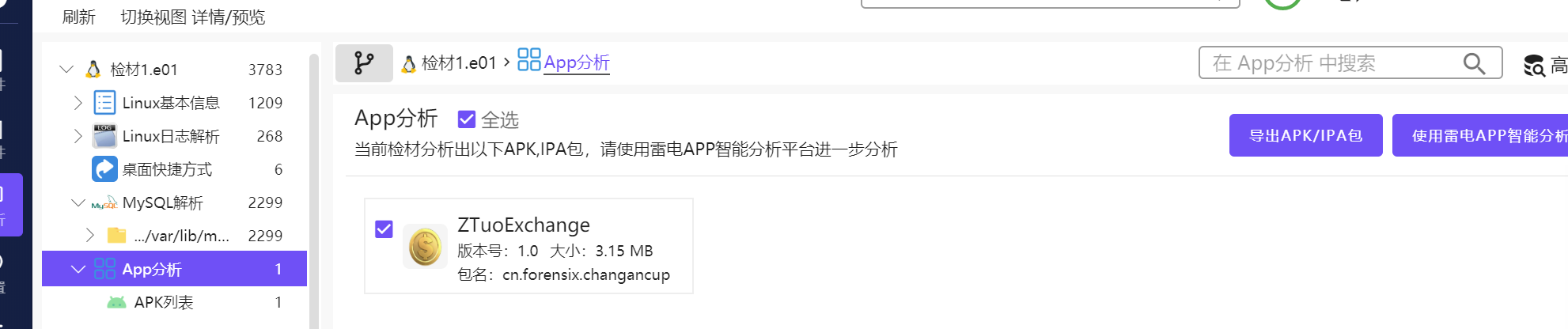
As for the package name, FireEye has it
cn.forensix.changancup
Download and analyze the apk via the link obtained from question 8

MATSFRKG
TDQ2UWP9

